I just had to set up a simple site to site VPN between a site with a fixed IP (SITE-B) and a site with a dynamic IP (SITE-A). Both routers are running the ‘Community Edition’ of pfSense and are installed on PC Engines APU.1C4. I have followed the documentation at pfSense.org about how to configure a Site To Site VPN with OpenVPN to get the VPN up and running. Because some things aren’t documented there I will put up my own HowTo here. Please do yourself a favour and read the documentation at pfsense.org first because it explains things in more detail than I will do here.
This HowTo will guide you trough the setup of:
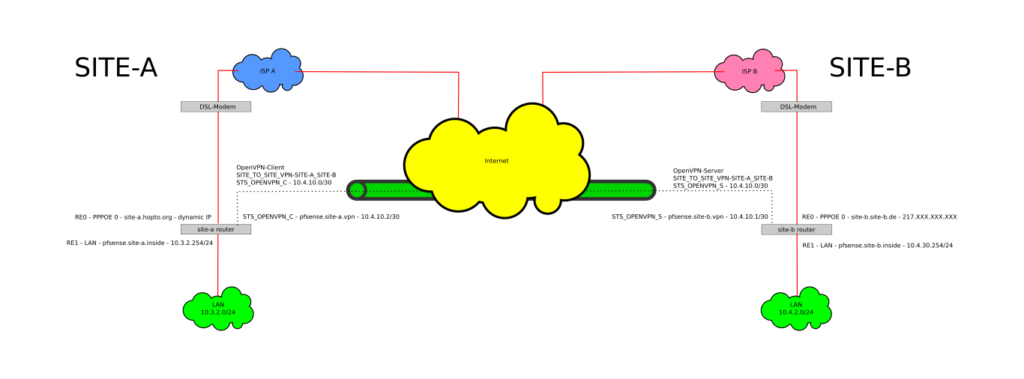
- An IPv4 ‘Site To Site VPN’ with OpenVPN on the pfSense platform (2.3.4 at time of writing) as seen in the schema above with the specific settings for the PC Engines APU hardware platform.
- The client will autoconnect to the server and (in the event of disconnection) reconnect automatically.
- The authentication between the client and the server will happen automatically via pre-shared key.
Sources:
Configure the OpenVPN server on SITE-B router
- Navigate to ‘VPN – OpenVPN‘
- On the ‘Servers‘-Tab click on the ‘+ Add‘-button to add a new server
- In the ‘General Information‘-section:
- Disable this server: ☐
- Server mode: Peer to Peer (Shared Key)
- Protocol: UDP
- Device Mode: tun
- Interface: set it to whatever external interface you want to have your OpenVPN server listening on. In my case this is ‘WAN‘.
- Local port: set it to the port you want the local OpenVPN server to listen on. Default is ‘1194‘.
- Description: Set an appropriate description e.g. ‘Site_To_Site-SITE-A_SITE_B‘
- In the ‘Cryptographic Settings‘-section:
- Automatically generate a shared key: ????
- Encryption Algorithm: AES-256-CBC (256 bit key, 128 bit block)
- Auth digest algorithm: RSA-SHA512 (512-bit)
- Hardware Crypto: No Hardware Crypto Acceleration (this is PC Engines APU specific, if your hardware has crypto support – enable it)
- In the ‘Tunnel Settings‘-Section:
- IPv4 Tunnel Network: 10.4.10.0/30 (this a very small subnet with 2 useable IP adresses since there is only one server and one client)
- IPv6 Tunnel Network: leave empty
- IPv4 Remote network(s): 10.3.2.0/24 (this is a comma separated list for all the networks you want to connect to on the client side (SITE A))
- IPv6 Remote network(s): leave empty
- Concurrent connections: 1
- Compression: Enabled with Adaptive Compression
- Type-of-Service: ☐ Set the TOS IP header value of tunnel packets to match the encapsulated packet value
- Duplicate Connection: ☐ Allow multiple concurrent connections from clients using the same Common Name
- Disable IPv6: ???? Don’t forward IPv6 traffic
- In the ‘Advanced Configuration‘-section:
- Custom options: leave empty
- Verbosity Level: default
- Click on ‘Save‘-button
You should now be forwarded to the list with your configured OpenVPN servers under ‘VPN – OpenVPN‘ on the ‘Servers‘-tab
- Click on the ‘Edit‘-button (the pencil) and leave this window open because we will need to copy the ‘Shared Key‘ from this form later.
Configure the OpenVPN client on SITE-A router
- Navigate to ‘VPN – OpenVPN‘
- Click the ‘Clients‘-tab
- On the ‘Clients‘-tab click the ‘+ Add‘-button to add a new OpenVPN client
- In the ‘General Information’-section:
- Disable this client: ☐
- Server mode: Peer to Peer (Shared Key)
- Protocol: UDP
- Device mode: tun
- Interface: Set to whatever external interface you want your OpenVPN client connect to the OpenVPN server at SITE-B. In my case this is ‘WAN‘.
- Local port: leave empty
- Server host or address: Set to the FQDN or IP address of the external SITE-B Interface. In this example it is ‘site-b.site-b.de‘.
- Server port: Set to the same port you have set in the server setup at SITE-B. Default is ‘1194‘.
- : leave empty
- : leave empty
- : none
- Infinitely resolve server: ????
- Description: Set an appropriate description e.g. ‘Site_To_Site-SITE-A_SITE_B‘
- In the ‘Cryptographic Settings‘-section:
- Peer Certificate Authority: nothing to do here
- Peer Certificate Revocation list: nothing to do here
- Automatically generate a shared key: ☐ – This will display a form field in which you can paste the key from the SITE-B server configuration.
Go back to SITE-B router. If you haven’t left the window open, navigate to ‘VPN – OpenVPN‘ and select the ‘Servers‘-tab, click on the ‘Edit‘-button (the pencil) next to the server you have created earlier
- In the ‘Cryptographic Settings‘-section:
- Copy everything from the ‘Shared key‘-field into your clipboard
Return to SITE-A OpenVPN client configuration
- In the ‘Cryptographic Settings‘-section:
- Paste the contents of your clipboard into the ‘Key‘-field
- Encryption Algorithm: AES-256-CBC (256 bit key, 128 bit block)
- Auth digest algorithm: RSA-SHA512 (512-bit)
- Hardware Crypto: No Hardware Crypto Acceleration (this is PC Engines APU specific, if you have hardware crypto – enable it)
- In the ‘Tunnel Settings‘-section:
- IPv4 Tunnel Network: 10.4.10.0/30
- IPv6 Tunnel Network: leave empty
- IPv4 Remote network(s): 10.4.2.0/24 (this is a comma separated list for all the networks you want to connect to on the server side (SITE B))
- IPv6 Remote network(s): leave empty
- Limit outgoing bandwidth: Set to whatever will fit your situation
- Compression: Enabled with Adaptive Compression
- Type-of-Service: ☐ Set the TOS IP header value of tunnel packets to match the encapsulated packet value
- Disable IPv6: ???? Don’t forward IPv6 traffic
- Don’t pull routes: ☐ Bars the server from adding routes to the client’s routing table
- Don’t add/remove routes: ☐ Don’t add or remove routes automatically
- In the ‘Advanced Configuration‘-section:
- Custom options: leave empty
- Verbosity Level: default
- Click on ‘Save‘-button
Assign an interface to the OpenVPN server on SITE-B
- Navigate to ‘Interfaces – (assign)‘
You will get a list of Interfaces which has a dropdown at the bottom end which is labeled ‘Available network ports‘
- Set ‘Available network ports‘ to ‘ovpns1 (your chosen description of your VPN)‘
- Click the ‘+ Add‘-button on the right
This will add a new Interface named ‘OPT<number>‘ to the list
- Click on ‘Save’-button
- Click on the name of the newly generated interface on the left (ususally the one with the highest trailing number)
This will open up the configuration for the interface which you have assigned to the OpenVPN server on SITE-B.
- In the ‘General Configuration‘-section
- enable interface: ????
- Description: STS_OPENVPN_S
- IPv4 Configuration Type: leave empty
- IPv6 Configuration Type: leave empty
- MAC Address: leave empty
- MTU: leave empty
- MSS: leave empty
- In the ‘Reserved Networks‘-section:
- Block private networks and loopback addresses: ☐
- Block bogon networks: ☐
- Click on ‘Save‘-button
- Click on ‘Apply Changes‘
Assign an interface to the OpenVPN client on SITE-A
- Navigate to ‘Interfaces – (assign)‘
You will get a list of Interfaces which has a dropdown at the bottom end which is labeled ‘Available network ports‘
- Set ‘Available network ports‘ to ‘ovpnc1 (your chosen description of your VPN)‘
- Click the ‘+ Add‘-button on the right
This will add a new Interface named ‘OPT<number>‘ to the list
- Click on ‘Save’-button
- Click on the name of the newly generated interface on the left (ususally the one with the highest trailing number)
This will open up the configuration for the interface which you have assigned to the OpenVPN server on SITE-B.
- In the ‘General Configuration‘-section
- enable interface: ????
- Description: STS_OPENVPN_C
- IPv4 Configuration Type: leave empty
- IPv6 Configuration Type: leave empty
- MAC Address: leave empty
- MTU: leave empty
- MSS: leave empty
- In the ‘Reserverd Networks‘-section:
- Block private networks and loopback addresses: ☐
- Block bogon networks: ☐
- Click on ‘Save‘-button
- Click on ‘Apply Changes‘
Firewall rules on SITE-B router
Now, to allow traffic to the OpenVPN server, a rule has to be added to the firewall on SITE-B router .
- Navigate to ‘Firewall – Rules‘
- Select the ‘WAN‘-tab
- Click the left ‘Add‘-button to add a rule to the top of the list
- In the ‘Edit Firewall Rule‘-section:
- Action: Pass
- Disable this rule: ☐
- Interface: WAN
- Address Family: IPv4
- Protocol: UDP
- In the ‘Source‘-section:
- Invert match:
- Dropdown: any
- In the ‘Destination‘-section:
- Invert match: ☐
- Dropdown: WAN address
- Destination Port Range: select OpenVPN (1194) in the left dropdown (that will also set the other dropdown to the same option
- In the ‘Extra Options‘-section:
- Log packets that are handled by this rule: ☐
- Description: Set an appropriate description like ‘ALLOW ANY to WAN ADDRESS:1194 (OpenVPN – SITE-A/SITE-B)‘
- Click the ‘Save‘-button
- Click ‘Apply Changes‘
Then add a firewall rule to allow traffic to pass through the tunnel.
- Stay at ‘Firewall – Rules‘
- Select the ‘OpenVPN‘-tab
- Click the left ‘Add‘-button to add a rule to the top of the list
- In the ‘Edit Firewall Rule‘-section:
- Action: Pass
- Disable this rule: ☐
- Interface: OpenVPN
- Address Family: IPv4
- Protocol: Any
- In the ‘Source‘-section:
- Invert match: ☐
- Dropdown: any
- In the ‘Destination‘-section:
- Invert match: ☐
- Dropdown: any
- In the ‘Extra Options‘-section:
- Log: ☐ Log packets that are handled by this rule
- Description: Set an appropriate description like ‘ALLOW ANY TO ANY on OPENVPN‘
- Click the ‘Save‘-button
- Click ‘Apply Changes‘
Firewall rule on SITE-A router
On SITE-A router a firewall rule to allow traffic to pass through the tunnel has to be added.
- Navigate to ‘Firewall – Rules‘
- Select the ‘OpenVPN‘-tab
- Click the left ‘Add‘-button to add a rule to the top of the list
- In the ‘Edit Firewall Rule‘-section:
- Action: Pass
- Disable this rule: ☐
- Interface: OpenVPN
- Address Family: IPv4
- Protocol: Any
- In the ‘Source‘-section:
- Invert match: ☐
- Dropdown: any
- In the ‘Destination‘-section:
- Invert match: ☐
- Dropdown: any
- In the ‘Extra Options‘-section:
- Log: ☐ Log packets that are handled by this rule
- Description: Set an appropriate description for the rule like ‘ALLOW ANY TO ANY on OPENVPN‘
- Click the ‘Save‘-button
- Click ‘Apply Changes‘
Restart OpenVPN service at SITE-B
- Navigate to ‘Status – OpenVPN‘
- In the ‘Peer to Peer Server Instance Statistics‘-section:
- Find the entry named ‘Site_To_Site-SITE-A_SITE_B UDP:1194‘ and click the ‘Restart openvpn Service‘-icon in the ‘Service‘-column
Restart OpenVPN service at SITE-A
- Navigate to ‘Status – OpenVPN‘
- In the ‘Client Instance Statistics‘-section:
- Find the entry named ‘Site_To_Site-SITE-A_SITE_B UDP‘ and click the ‘Restart openvpn Service‘-icon in the ‘Service‘-column




Finally a manual that completely explained all the steps!
The only one i found searching.
thanks a lot!
indeed this manual works and is really helpful.
ps. please put attension once you are masking your subnets with remote networks, it can bring some headache with further troubleshooting once typo is made
great guide. really useful..
1 question though – Why are the firewall rules put on the openvpn tab and not on the interface tab? Would this not affect all other vpns setup on the firewall as well?
Hi Arnie,
I will have a look into that when I have time. Please be patient, it will take a couple of days.
H
I would love to know this also. I have been using Pfsense for many years. I have setup many OpenVPN servers, site to site, and roadwarrior and I have never needed to add or use the interface for OpenVPN to set rules. I only use the automatically created one.
Hello Arnie,
I hadn’t noticed that, thanks for your feedback. I will add a link and a note to the guide.
When I built this setup for my customer and wrote the guide, I guess I didn’t pay attention. Of course it makes much more sense to put firewall rules on the individual VPN interfaces. But since the customer doesn’t need more VPNs, it doesn’t matter in this case.
You are right. Configuring firewall rules on the ‘OpenVPN‘-tab will affect all configured VPNs (OpenVPN). For reference: https://docs.netgate.com/pfsense/en/latest/vpn/openvpn/openvpn-traffic-filtering.html
=)
First of all i want to thank you for providing such a wonderful information and request you to keep updating in future.
Thanks